The straight way to secure device software applications
The world is evolving fast with AI and IoT technology development. Cutting-edge technologies generate massive data, and data privacy becomes an important theme. AI-driven smart devices and autonomous hardware level security become the 2023 megatrend. IBM reported the average data cost of a data breach was $4.5 million in 2022. This impact corporate CxOs to start to consider how to avoid potential embedded security on their devices and manage the crisis in advance to prevent future brand reputation damage and business destruction.
Ensuring that you have high-quality code is a mandatory step in making sure that your device is secure. And using code analysis tools as an integrated part of your development process is a vital step. The quality of the product depends on the quality of the source code. On top, you also need to ensure that you have security implemented from inception, so that all aspects of your development, manufacturing, and update flows work together to ensure that your product is secure.
Security legislation and codes of practice
With the rising of securing devices, the global embedded security market is estimated to $17.03 billion by 2029 according to Fortune Business Insight. Many regional organizations and governments have set up various security legislation to define the security standards for devices such as the EU Cyber Resilience Act, FDA legislation in the US, Auto Data Security Compliance and Practice Guidance in China, and New International Standard for Safe Use of IoT Products and Systems in Japan.
Culture Media and Sport provides 13 Guidelines for Consumer IoT Security, which is being used for the basis for much of the legislation being drawn up around the globe. IoT Security Foundation (IoTSF) also released the “Consumer IoT Security Quick Guides” 2 which are intended to help global organizations to better understand and comply with the various new international standards, regulations and national guidance on consumer IoT security.
Device vendors who want to export their devices to different regions across the world need to make their products to meet legislation requirements. The blind for this various security legislation could cause device redundancy and business loss.
IP theft is a major concern
Taking a step back from guidelines and legislation, there are several other important drivers for wanting to increase the level of security in your device product. Back in September 2019, we asked our customers what their number one security concern was, and here is what they said
:
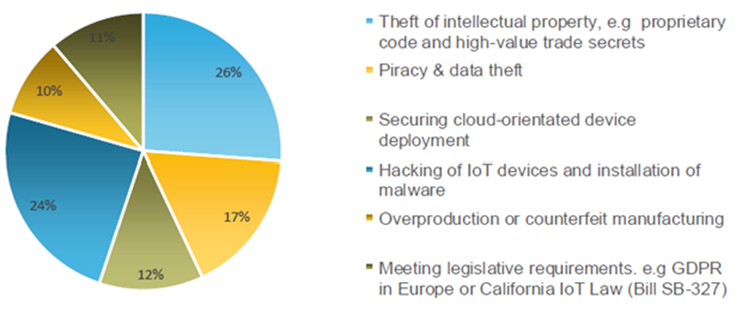
Figure 1: What is your number 1 security concern?
So obviously meeting legislative requirements is on there. But the other major concern for our customers was intellectual property (IP) theft, followed by hacking devices and installation of malware as you can see in the graphics. What is the effect of intellectual property theft? Data breaching, and device cloning, and could cause huge damage to the brand reputation.
Therefore, an important part of adding security to your device product should be including some form of “IP protection”. This should protect your software from unauthorized access by hackers or competitors and prevent your software from being stolen during production or once your devices are in the field.
When to add embedded security?
If we consider a typical development in manufacturing flow, it might be something like this:
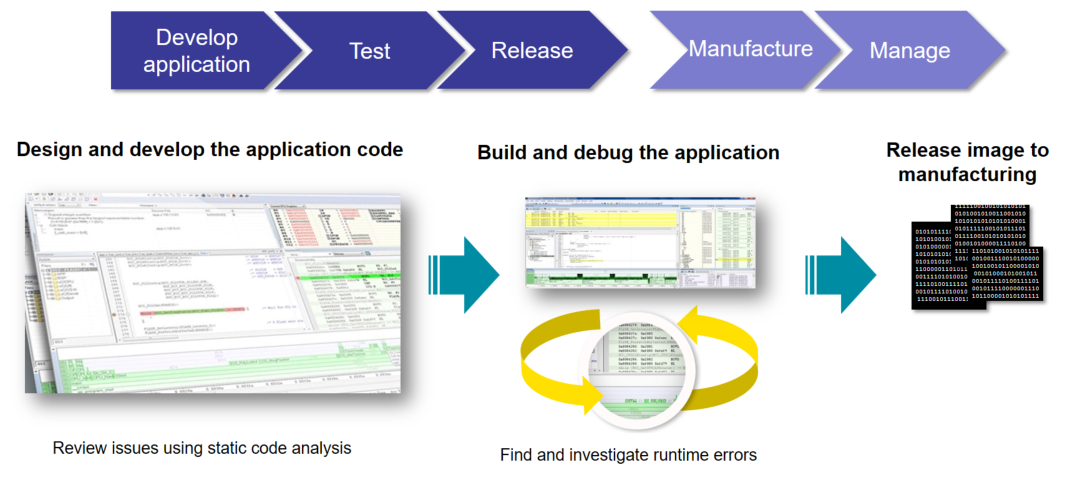
Figure 2: A traditional software development flow
You could implement security at any stage of the development process with IAR security tools to meet your different requirements for security levels. However, the security level is normally lower if you implement security functions in the late development stage than from the inception.
Security baked into your product
It is much better to include security right from the concept design stage of your project so that security functions are baked into your product and your device can get full security function supports through the overall lifecycle, which means, the best way is to have security fully integrated into your development tools and their workflow, then you can be developing and testing with security measures already integrated into your product – greatly reducing the risk once your device is delivered to end-users.
The basis of a secure device is the implementation of a Root of Trust (RoT). This is generally the minimal set of software, hardware, and data that you can trust. On the hardware side, the MCU being used needs to have the ability to disable debug (at the time of production), have the capability of locking the memory and provide a unique identity. On the software side, a secure boot manager builds upon the underlying MCU hardware capabilities to provide a robust root of trust for a device, securing the overall boot process, protecting the device against the injection of malicious software, and enabling and protecting a secure update mechanism.
Adding in security data, such as Public Key Infrastructure (PKI) keys and certificates, provides the MCU system with its security context profile which should be provisioned into each device. This can all be made straightforward by using a development tool that can create and configure the elements of the security context using its knowledge of the capabilities of the MCU device being targeted.
Once the MCU is provisioned with its security context, the main development team can get on with developing reliable and high-quality code from the main user application. If knowledge of security is built into the development tools being used, then the workflow being followed by the engineers carrying out this development work should be mainly unchanged from that which would be followed for a system without security. And this should help to ensure that development and testing timescales remain unaffected.
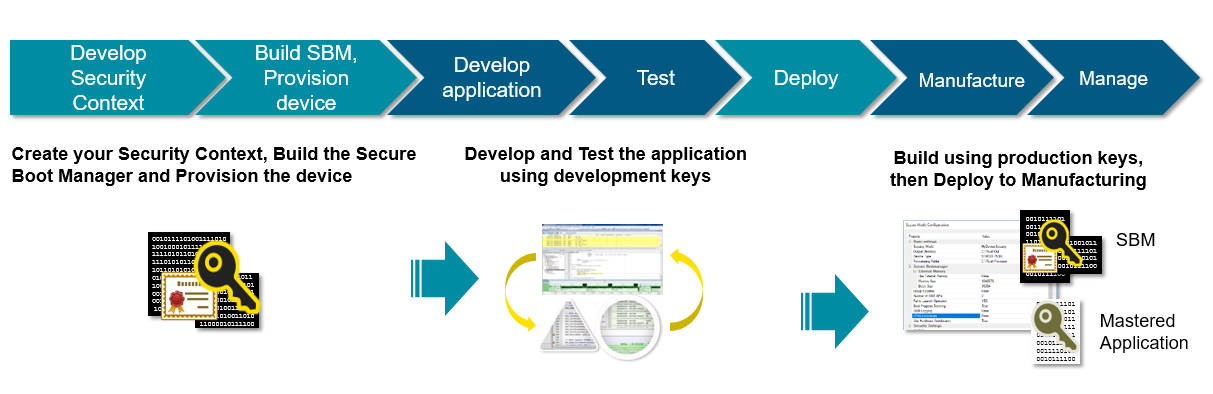
Figure 3: Software development flow with security
Once development of the future-proof code and test are complete, the final production security context and encrypted application will need to be delivered to your secure programming facility, or for small runs perhaps using a secure desktop programming system. But again the tools and facilities being used here are key to ensuring that your device stays secure.
Summary
Driven by security legislation and concern about business reputation damage, more businesses are starting to look at security implementation into their devices.
High-quality code analysis tools combined with the use of coding standards are designed to promote secure coding practices. By building on top of code quality, the available security measures, such as encrypting the codebase and setting manufacturing limits, will substantially reduce the risk of counterfeiting and cloning during production aside from the security legislation compliance. Device security needs to be straightforward, scalable, and simple.
Written by Andy Beeson, Ada Lu / Product Marketing Senior Manager, Embedded Security Solutions, IAR Systems
References
- https://www.gov.uk/government/publications/code-of-practice-for-consumer-iot-security
- https://www.iotsecurityfoundation.org/
- https://www.gartner.com/en/newsroom/press-releases/2020-09-01-gartner-predicts-75--of-ceos-will-be-personally-liabl