嵌入式创新的步伐正在加快,需要灵活、可扩展和安全的解决方案。IAR 软件开发平台可统一工作流程、简化流程并确保合规性,帮助团队提高生产力与质量。

现代软件开发团队的平台
了解 IAR 平台如何帮助您
嵌入式开发的变革
了解 IAR 的软件开发平台如何优化工作流程,确保合规性,并加速开发。从云短到高级调试,IAR 提供的全面解决方案使团队能够自信地进行创新。
愿景
拓展嵌入式开发
长期以来,IAR 一直处于嵌入式软件开发的前沿,提供可靠的解决方案,帮助团队应对行业的复杂性。随着人工智能、物联网和云驱动工作流程的发展,团队需要灵活、可扩展且安全的工具,以保持竞争优势。
传统的解决方案已不再满足需求。团队需要能够自由选择工具、简化工作流程并确保安全的解决方案,同时加快产品的上市速度。这就是为什么 IAR 已经超越了编译器和调试器的范畴,发展成为现代软件开发团队的平台,致力于提供统一的开发、自动化和安全的创新解决方案。
通过灵活性与自动化,实现开发现代化转型
借助基于云的工作流程以及 IAR Build Tools 的不断进化,我们正转向以结果为导向的解决方案,支持持续优化开发效率,并通过灵活的授权模式实现成本可控与可预期。
IAR 提供按用户名和按容量计费的多种授权方式,帮助团队无缝使用开发工具,同时高效整合 CI/CD 流程,全面支持 Kubernetes、GitLab、GitHub、Bitbucket 和 Docker 等平台,实现大规模编译、链接与调试的自动化。
通过融合云端开发能力、CI/CD 自动化、经过认证的工具链以及领先的安全技术,IAR 助力团队实现规模化开发、加速创新、提升生产力,并在产品开发早期就实现漏洞检测、合规管理与安全制造,满足汽车、工业、医疗、消费电子等关键行业的高标准需求。
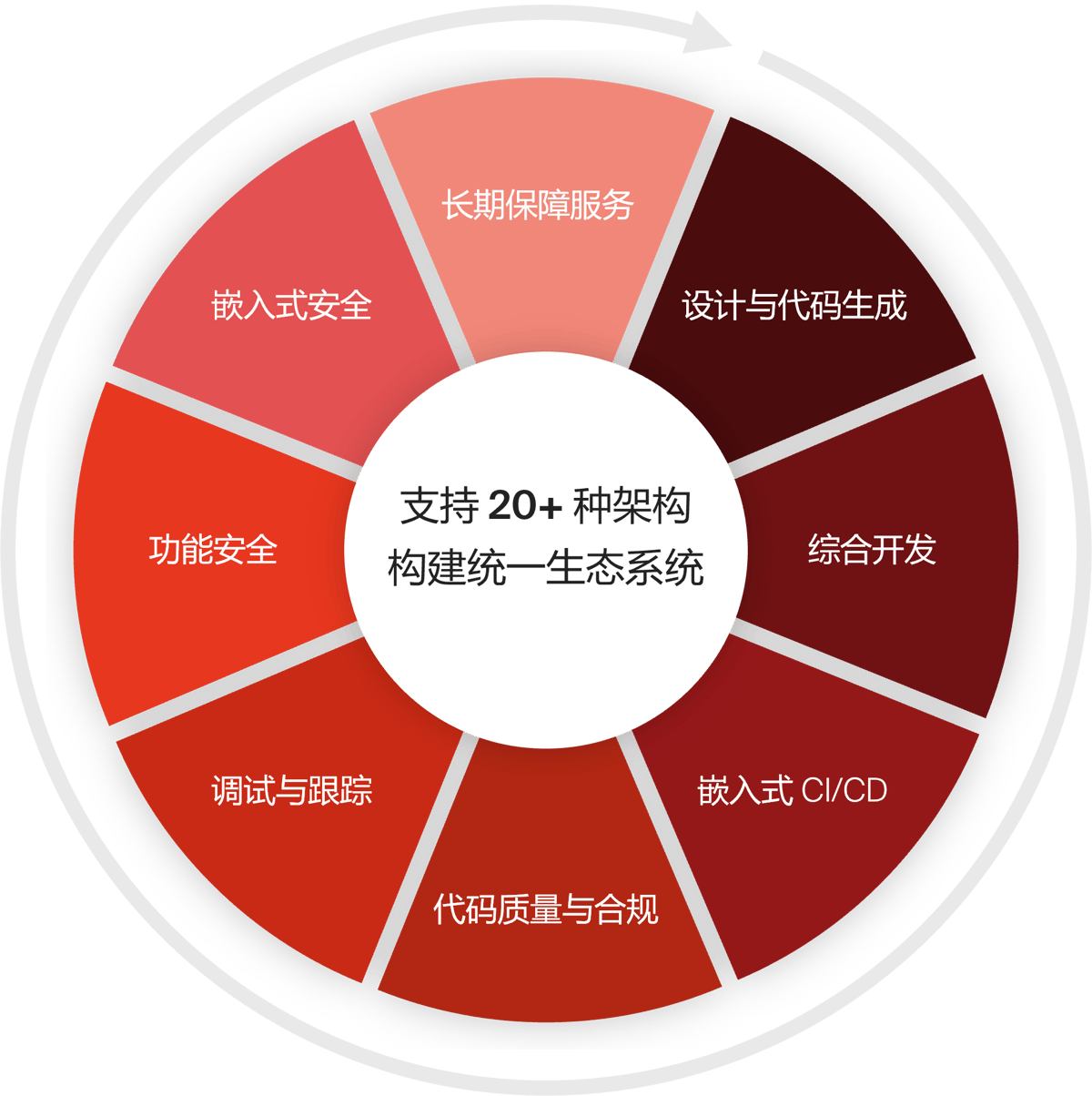
解决方案
我们的 关键解决方案

设计与代码生成

综合开发
将编码、构建、调试和测试统一在一个平台中,降低整个开发生命周期的复杂性并提高团队效率。

嵌入式CI/CD
通过Kubernetes、Jenkins、GitHub和GitLab集成实现自动化测试和部署,优化工作流程,提升开发效率,缩短开发周期。

代码质量与合规

调试和跟踪

功能安全

嵌入式安全

长期保障服务
深受行业领先企业的信赖
- 10
满足10项功能安全认证标准
- 20+
支持20+种架构
- 30
您每天与我们客户生产的产品互动的次数
- 40+
40多年稳健经营
- 70+
70多家半导体合作伙伴
- 15k+
支持超过15000款芯片
嵌入式开发平台
我们的解决方案如何帮助您
自由灵活地扩展开发操作,通过确保代码质量,加速创新进程,并在加强安全性的同时简化合规性。
广泛的架构和芯片支持
支持 20 多种架构,畅享无限可能
IAR 的开发平台支持多种架构,如 Arm 和 RISC-V 等,确保兼容性,避免依赖单一供应商,简化传统和下一代嵌入式系统的开发。

云兼容,专为企业量身定制
支持云开发,实现无缝扩展

始终包含功能安全
从项目开始就确保功能安全合规
通过功能安全认证的工具确保符合 ISO 26262、IEC 61508 和 IEC 62304 等标准,降低认证复杂性,帮助团队在汽车、工业和医疗等行业中构建安全可靠的安全关键型应用。

端到端的嵌入式安全
在每个阶段确保嵌入式系统的安全
了解如何运作
IAR 平台有何独特之处?
观看平台演示,了解我们如何支持 DevOps 集成、功能安全与信息安全、灵活授权、多架构开发,以及即使在产品发布多年后仍可实现快速且可重复的构建流程。
视频
助力企业创新
探索如何简化工作流程、采用云解决方案并确保不同架构的功能安全。观看视频,了解 IAR 如何帮助团队更智能、更快速地进行开发。
利用容器化和云解决方案实现一致的工作流程
拓展开发规模,确保功能安全,实现长期成功
支持多种架构,统一开发流程
行业
为满足特定行业需求而设计的开发平台
IAR 的平台提供全面的解决方案,涵盖汽车、工业、医疗、机械控制等领域,确保开发团队能够满足法规、安全和性能方面的要求。
![[ZH] Industries | Automotive](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/industry%20automotive%20car%20wheel%20and%20robot%20arm.jpg?width=600&height=338&name=industry%20automotive%20car%20wheel%20and%20robot%20arm.jpg)
汽车
通过 TÜV SÜD 认证的工具、静态代码分析和安全开发,IAR 确保满足 ADAS、动力总成和电动汽车应用的 ISO 26262 要求,提供功能安全和安全性保障。
![[ZH] Products | Industries | Industrial Automation](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/industrial%20automation%20robot%20arm%20engineer%20with%20touchpad%20lighter%20mode%20for%20hero%20image.jpeg?width=600&height=316&name=industrial%20automation%20robot%20arm%20engineer%20with%20touchpad%20lighter%20mode%20for%20hero%20image.jpeg)
工业
使用 IAR 开发平台实现更高的生产力,更快的创新过程,以及安全的自动化。
![[ZH] Industries | Medical](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/Medical%20doctor%20infront%20of%20screen%20with%20lungs%20%20on%20display%20to%20the%20left.jpeg?width=600&height=336&name=Medical%20doctor%20infront%20of%20screen%20with%20lungs%20%20on%20display%20to%20the%20left.jpeg)
医疗
为您的医疗设备嵌入式项目提供支持,使其符合标准。我们的解决方案可确保代码质量,实现安全、高效、按时交付的应用 。
![[ZH] Industries | Machinery control](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/switchboard.jpg?width=600&height=400&name=switchboard.jpg)
机械控制
为您的嵌入式项目提供精准高效的机械控制功能。我们的解决方案确保代码质量,助力安全、高速、精准的系统运行。
![[ZH] Industries | Household appliance](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/household%20appliance%20smart%20home%20screen%20on%20sofa%20table.jpg?width=600&height=338&name=household%20appliance%20smart%20home%20screen%20on%20sofa%20table.jpg)
家用电器
为您的家电嵌入式项目赋能。我们的解决方案确保代码质量,实现安全、高效、按时交付的应用。
客户案例
将挑战转化为成功
了解世界领先企业如何利用我们的平台加强嵌入式开发。
Casio — 加快上市时间
阅读案例尽管我们提升了性能,但我们也必须保持功耗,这就是为什么我们将处理分成了两个核心。这是一项艰巨的工作,但我们成功地在提升性能和功耗效率之间找到了平衡。
Osong 医疗创新基金会 – 确保医疗软件认证
阅读案例质量和认证对高科技医疗设备的未来至关重要。通过使用 C-STAT,我们能够提升代码质量,同时为符合 IEC 62304 认证的功能安全升级做好准备,以满足监管标准。
NEWGIN – 强化未来软件质量
阅读案例随着固件复杂度的提升,我们越来越需要能够保障软件质量的工具。静态代码分析和CI工具集成将成为提升可靠性并保持高开发标准的关键。
VICTEK – 面向安全物联网系统的高质量代码
阅读案例开发低功耗物联网系统需要无缺陷的高质量代码,以确保与优化的应用和网络安全集成,同时最大程度降低网络安全风险。
Landis+Gyr – 通过静态代码分析实现早期缺陷检测
阅读案例为了保持高产品质量,我们需要能够在开发早期发现缺陷的工具。C-STAT 让我们更快找到漏洞,缩短上市时间,并优化开发成本,使其成为我们各个站点的核心工具。
支持的芯片

了解更多信息?
学习文章
常见问题解答
IAR 的平台如何在多个架构上优化开发流程,而无需重新调整工具链?
IAR 的平台支持 20 多种架构,包括 Arm、RISC-V、AVR、RL78 和 8051,提供统一的工具链,避免了切换开发环境的繁琐操作。
如何将 IAR 的工具集成到现有的 CI/CD 中,提升自动化水平?
IAR 可与 Jenkins、GitHub、GitLab 和 Kubernetes 集成,实现自动构建和持续测试。
IAR 的平台如何降低开发成本并加快不同项目的上市时间?
通过统一工作流程并支持自动化,IAR 的平台可减少调试时间,降低重复工作及返工成本,并降低安全认证相关时间及成本。
嵌入式开发平台避免对单一供应商的依赖,有哪些商业优势?
单一供应商可能限制灵活性并增加成本。IAR 的平台确保团队能够跨不同的微控制器和架构进行开发。
IAR 的长期保障与支持如何帮助我们确保嵌入式产品的未来适用性?
IAR 可提供扩展维护、合规性更新和迁移支持,确保软件在硬件演进过程中保持可持续性。





