The pace of embedded innovation is accelerating, requiring flexible, scalable, and secure solutions. IAR’s platform unifies workflows, streamlines processes, and ensures compliance, helping teams eliminate inefficiencies and improve quality across industries.

The platform for modern software development teams
How it works
Transforming embedded development
Discover how IAR’s platform streamlines workflows, ensures compliance, and accelerates development. With a comprehensive palette of solutions, from cloud connectivity to advanced debugging, it empowers teams to innovate with confidence.
Vision
Scaling embedded development
IAR has long led embedded software development, providing trusted solutions to help teams navigate industry complexities. As AI, IoT, and cloud-driven workflows evolve, teams need flexible, scalable, and secure tools to stay ahead.
Traditional solutions no longer suffice. Teams must freely choose tools, streamline workflows, and ensure security while accelerating time-to-market. That’s why IAR has evolved beyond compilers and debuggers into the platform for modern software development teams, built on a transformative palette of solutions that unify development, automation, and security.
Modernizing development with flexibility and automation
With cloud-based workflows and an evolution of IAR Build Tools, we are shifting to outcome-driven solutions that foster continuous improvement and predictable costs through our flexible offer.
IAR provides named user and capacity-based licensing, allowing teams to seamlessly access tools while optimizing CI/CD workflows across Kubernetes, GitLab, GitHub, Bitbucket, and Docker for scalable compilation, linking, and debugging.
By integrating cloud-ready development, CI/CD automation, certified toolchains, and advanced security, we help teams scale, innovate, and boost productivity while ensuring early vulnerability detection, compliance, and secure manufacturing, essential for all key industries.
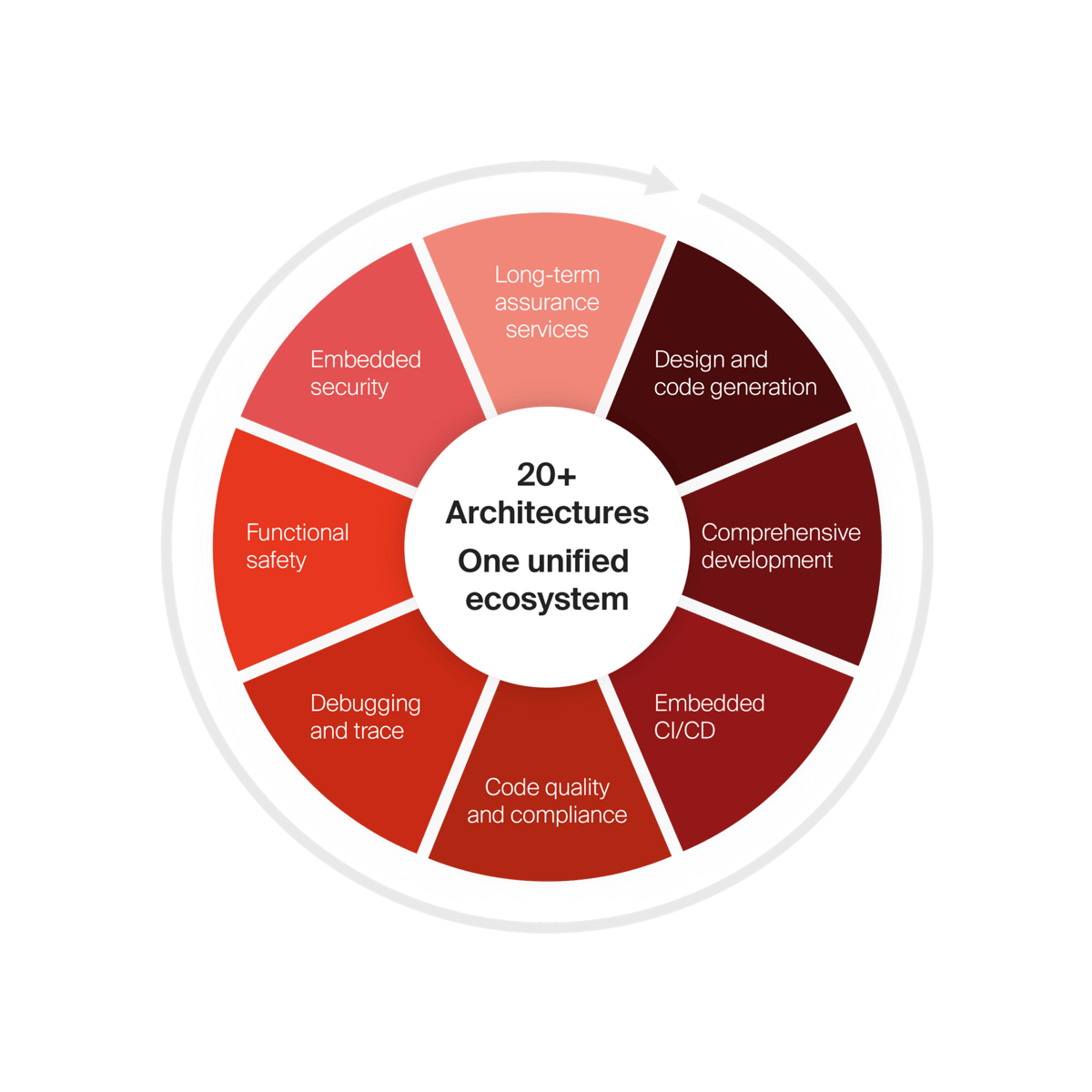
Solutions
Our key solutions

Design and code generation

Comprehensive development

Embedded CI/CD

Code quality and compliance

Debugging and trace

Functional safety

Embedded security

Long-term assurance services
Trusted by industry leaders: IAR in numbers
- 10
pre-certified standards
- 20+
architectures
- 30
times a day you interact with a product made by one of our customers
- 40+
years in business
- 70+
semiconductor partners
- 15k+
supported devices
The platform for embedded development
How our solutions help you
Scale development operations with freedom and flexibility, accelerate innovation with code confidence, and simplify compliance while strengthening security.
Architecture and device agnostic
Develop without limits on 20+ architectures

Cloud-ready, tailored for enterprises
Scale seamlessly with cloud-powered development

Functional safety always included
Ensure safety compliance from the start

End-to-end embedded security
Secure your embedded systems at every stage
See how it works
What makes the IAR platform different?
See the platform in action and learn how it supports DevOps integration, built-in functional safety and embedded security, flexible licensing, multi-architecture development, and faster, repeatable builds even years after release.
Explainer video
Driving enterprise innovation
Explore how to streamline workflows, adopt cloud-native solutions, and ensure functional safety across diverse architectures. Watch the videos to learn how IAR helps teams develop smarter and faster.
Enabling consistent workflows with containerized and cloud-native solutions
Managing diverse environments and scaling workflows across distributed teams can be overwhelming. Without standardized build environments, maintaining consistency and efficiency becomes a challenge. IAR’s platform supports containerized development and cloud-native workflows, enabling reproducible environments, automation, and scalability. With CI/CD integration, teams can streamline development, improve collaboration, and accelerate time-to-market.
Scaling development and ensuring functional safety for long-term success
Supporting diverse architectures and unifying development workflows
Siloed tools and vendor-specific dependencies slow down development. IAR’s unified platform bridges gaps across architectures, enabling seamless collaboration and efficient workflows. With advanced debugging, automation, and CI/CD integration, teams can accelerate development, improve efficiency, and reduce project delays—keeping innovation on track.
Industries
The platform designed for industry-specific needs
IAR’s platform delivers a comprehensive palette of solutions across automotive, industrial automation, medical, machinery control, and more—ensuring development teams stay ahead of regulatory, security, and performance demands.
![[EN] Industries | Automotive](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/car%20with%20the%20lights%20on%20back%20and%20grey.png?width=600&height=338&name=car%20with%20the%20lights%20on%20back%20and%20grey.png)
Automotive
Ensure functional safety and security with TÜV-certified tools, static analysis, and secure development, meeting ISO 26262 requirements for ADAS, powertrain, and EV applications.
![[EN] Products | Industries | Industrial Automation](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/industrial%20automation%20robot%20arm%20engineer%20with%20touchpad%20lighter%20mode%20for%20hero%20image.jpeg?width=600&height=316&name=industrial%20automation%20robot%20arm%20engineer%20with%20touchpad%20lighter%20mode%20for%20hero%20image.jpeg)
Industrial automation
Deliver high-quality, efficient, and reliable embedded systems that enhance the industrial automation processes.
Medical
Empower your embedded projects for medical devices and be compliant. Our solutions ensure code quality for safe, fast, and on-time applications.
![[EN] Industries | Machinery control](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/switchboard.jpg?width=600&height=400&name=switchboard.jpg)
Machinery control
Unleash the power of machinery control with embedded technology. Our comprehensive range of solutions is designed to address this effectively.
![[EN] Industries | Household appliance](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/household%20appliance%20smart%20home%20screen%20on%20sofa%20table.jpg?width=600&height=338&name=household%20appliance%20smart%20home%20screen%20on%20sofa%20table.jpg)
![[EN] Industries | Household appliance](https://143667342.fs1.hubspotusercontent-eu1.net/hub/143667342/hubfs/WEB%202025/Images/Industries/industries-household-appliance-4x5.jpg?width=600&height=750&name=industries-household-appliance-4x5.jpg)
Household appliance
Empower your embedded projects for the household appliance, from automated processes to user inputs. Our solutions ensure code quality for safe, fast, and on-time applications.
Customer cases
Transforming challenges into success
Get inspiration on how world-leading companies enhance their embedded development with our platform.
Casio — Improving time to market
Read caseAlthough we increased performance, we also had to maintain power consumption, which is why we divided processing into two cores. It was a lot of work, but we were able to find a balance between improved performance and power efficiency.
Osong Medical Innovation Foundation – Ensuring medical software certification
Read caseQuality and certification are critical for the future of high-tech medical devices. By using C-STAT, we can improve code quality while preparing for IEC 62304-certified functional safety upgrades to meet regulatory standards.
NEWGIN – Strengthening software quality for the future
Read caseAs firmware complexity grows, we see an increasing need for tools that help ensure software quality. Static analysis and CI tool integration will be key to improving reliability and maintaining high standards in development.
VICTEK – High-quality code for secure IoT systems
Read caseDeveloping low-power IoT systems requires defect-free, high-quality code to ensure secure integration with optimized applications and networks, while minimizing cybersecurity risks.
Landis+Gyr – Early bug detection with static analysis
Read caseTo maintain high product quality, we need tools that catch defects early in development. C-STAT allows us to find bugs faster, reduce time to market, and streamline development costs, making it a core tool across our sites.
Supported devices

Interested to know more?
Blog posts

Escaping the hidden costs of inconsistent CI/CD in regulated systems

Why Zephyr RTOS with IAR is a smart choice for embedded teams

Enabling memory-safe C/C++ development without a language shift
A new chapter for our Docker support: Introducing the IAR cloud-ready containers repository

Breaking the CI/CD bottleneck: Scaling Embedded DevSecOps with containers and automation
FAQ
How can IAR’s platform help in streamline development across multiple architectures without reworking toolchains?
IAR’s platform supports over 20 architectures, including Arm, RISC-V, AVR, RL78 and 8051, providing a unified toolchain that eliminates the need for switching environments.
What’s the best way to integrate IAR’s tools into an existing CI/CD pipeline to improve automation?
IAR integrates with Jenkins, GitHub, GitLab, and Kubernetes, enabling automated builds and continuous testing.
How does IAR’s platform reduce development costs and speed up time-to-market across different projects?
By unifying workflows and enabling automation, IAR’s platform cuts down debugging time, reduces rework, and minimizes certification costs.
What are the business advantages of using a vendor-agnostic embedded development platform?
Vendor lock-in can limit flexibility and increase costs. IAR’s platform ensures teams can work across different microcontrollers and architectures.
How does IAR’s long-term support help us future-proof our embedded product lifecycle?
IAR can provide extended maintenance, compliance updates, and migration support, ensuring software sustainability as hardware evolves.
Resources