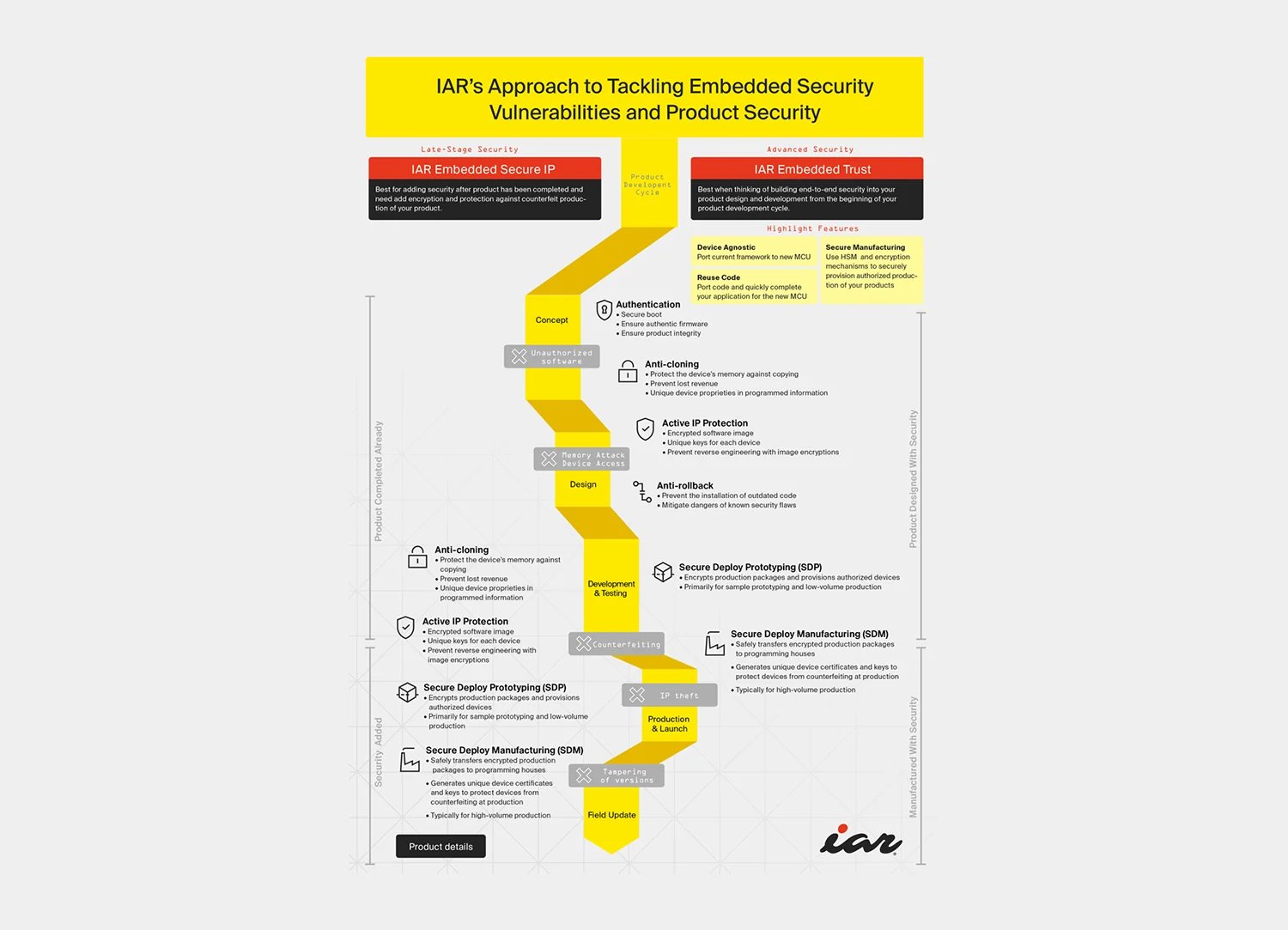
IAR Embedded Trust
Secure your code, applications, and devices right from the start by simplifying embedded security with the Root of Trust.

01
Authenticity
We verify authorized software code and application installation to protect your IPs from the root and ensure the cryptographic methods are applied to your chips and devices. You will have the Root of Trust quickly.
02
Active IP protection
We promise critical key management to lock your applications onto authorized devices, providing secured applications and devices access right from the boot process.
03
Anti-cloning
We support unique identification for software applications and device hardware, preventing counterfeits and encrypting your manufacturing.
04
Anti-rollback
We manage your software update processes to provide protection against roll-back attacks and versioning threats.
Product overview
With the complete embedded security features, IAR Embedded Trust meets your demands to protect software and devices once you power on the booting system. You will implement industry-leading security solutions and achieve security compliance quickly.
Please accept marketing and preference cookies to view this video.
Modify settings.Supported devices
Our security tools and services offer support for a wide range of devices, including Arm-based MCUs from STMicroelectronics, Renesas, NXP, Microchip, Silicon Labs, Nordic and Infineon*, as well as the Renesas RX MCU family devices, enabling you to choose the right MCU for the security and functional needs of your application. In addition, support for the vast majority of MCUs can be achieved through the use of Hardware Abstraction Layer (HAL).
*Contact us for details on the Infineon device support included in IAR Embedded Secure IP
The device families in the list are ported and tested by us. Notice that some specific device variants might not have been tested.
We are constantly updating our growing list of supported devices. If your device is not listed here, contact us to find out when your device will be supported.
| STMicroelectronics | Renesas | Microchip | NXP | Silicon Labs | Nordic |
|
STM32F4x STM32F7x STM32G0C1xE STM32G474xE STM32H7x STM32L4x STM32L5x STM32U5x STM32WB5x |
RA2xx (RA2L1) RA4Mx (RA4M2) RA6Mx (RA6M3) RX6xx (65N/66T) RX7xx (72M/72N/72T)
|
SAML11 PIC32CM5164LSx0 |
K2x K6x KV5x LPC55x i.MXRT10x4 |
EFM32xG22 EFR32xG23 |
NRF52840 |
Get quote
Want to use this product in your development projects? Our sales team is here to guide you to the right solution. Complete this form, and we will get back to you with a price quote tailored to your needs.