Product
IAR Embedded Trust
Embedded security is inlcuded in IAR's platform
IAR Embedded Trust is an end-to-end embedded security solution designed to safeguard software, hardware, and production environments against evolving security threats.
Key benefits
IAR Embedded Trust ensures trusted execution, authenticated updates, and threat protection, enabling secure firmware deployment and lifecycle management to help developers meet security requirements with confidence.


Secure firmware updates

Security contexts
Features
IAR Embedded Trust protects against unauthorized access, cloning, and firmware tampering, ensuring trusted boot, secure provisioning, and seamless integration for enhanced device security and integrity

Immutable boot process

Secure provisioning

Seamless integration

Flexible security management
SESIP Level 1 certification

Supported devices
| ST | Renesas | Microchip | NXP | Silicon Labs | Nordic |
|
STM32F4x STM32F7x STM32G0C1xE STM32G474xE STM32H7x STM32L4x STM32L5x STM32U5x STM32WB5x |
RA2xx (RA2L1) RA4Mx (RA4M2) RA6Mx (RA6M3) RX6xx (65N/66T) RX7xx (72M/72N/72T) |
SAML11 PIC32CMx |
K2x K6x KV5x LPC55x i.MXRT10x4 |
EFM32xG22 EFR32xG23 |
NRF52840 |
Blog posts
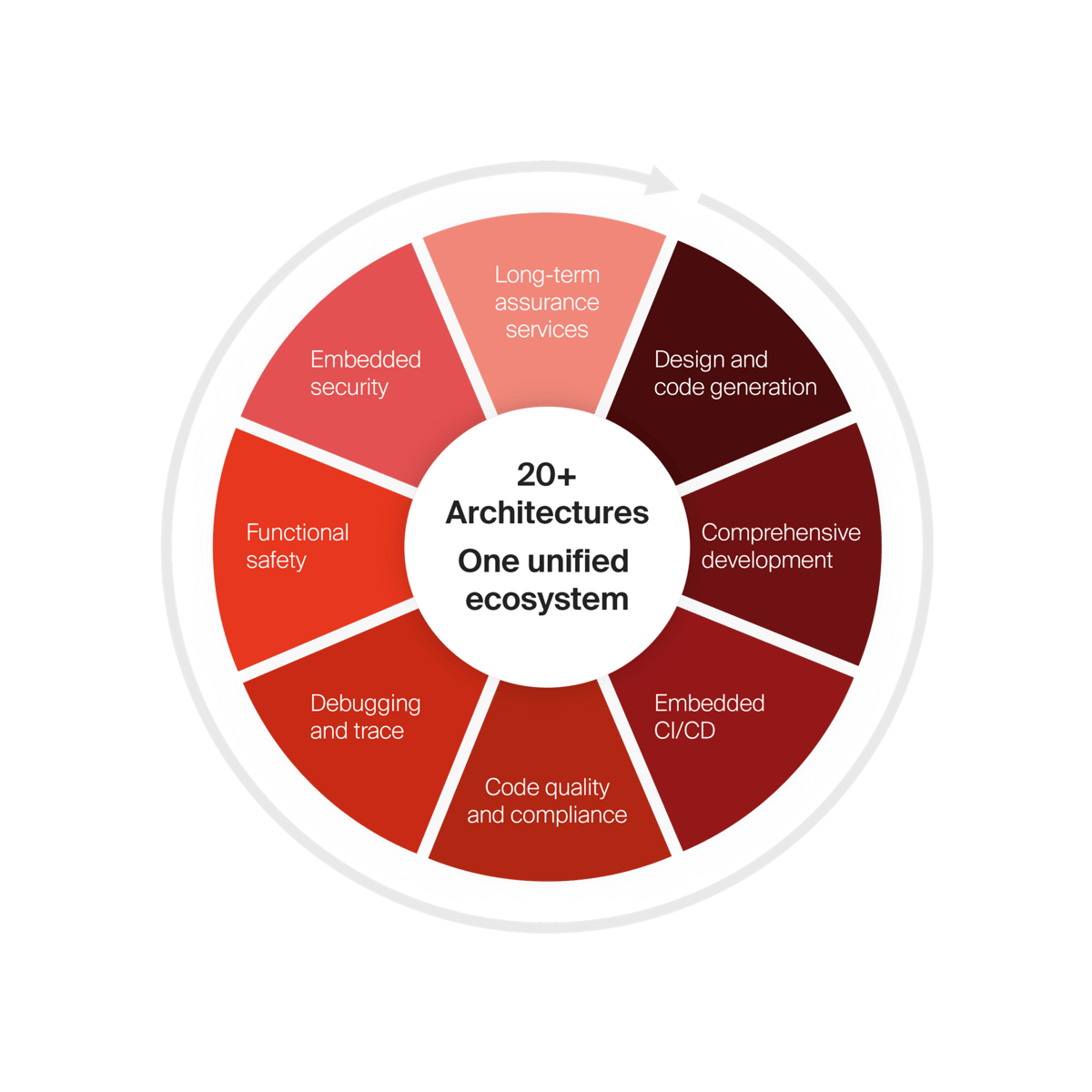
IAR embedded development platform
Get access to all
Scale development operations with freedom and flexibility, accelerate innovation with code confidence and simplify compliance while strengthening security.
- Architecture and device agnostic
- Cloud-ready, tailored for enterprises
- Functional safety always included
- End-to-end embedded security
With our platform, you get access to everything.


